Fortinet Cloud Security Best Practices: Tips for Securing Cloud Environments Using Fortinet
Introduction
As more organizations adopt cloud platforms, securing these environments becomes increasingly critical. Fortinet offers a comprehensive suite of tools tailored to help businesses secure their cloud infrastructure. Here’s a deep dive into best practices for securing your cloud environment using Fortinet:
Enable Zero Trust Architecture
What is Zero Trust? Zero Trust is a security model that assumes no one, whether inside or outside the network, can be trusted by default. With the shift to the cloud, where traditional network perimeters are no longer applicable, adopting a Zero Trust approach helps mitigate potential security risks.
Fortinet’s Role in Zero Trust: Fortinet facilitates a Zero Trust model through its Identity and Access Management (IAM) solutions, including FortiAuthenticator and FortiToken. These tools ensure that every user, device, and application attempting to access sensitive cloud data undergoes thorough identity verification. Use multi-factor authentication (MFA) and role-based access controls (RBAC) to enhance security layers further.
Implementation Tip: Ensure that all users, whether internal or external, access data and applications through secure, authenticated connections. Fortinet’s Zero Trust Network Access (ZTNA) solutions can secure cloud workloads by verifying both user identity and device health.
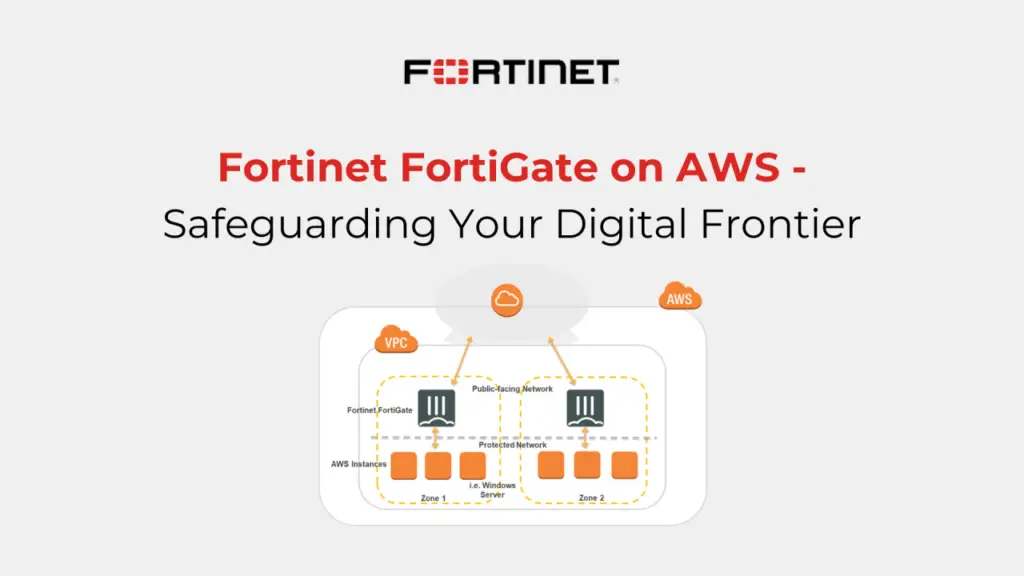
Deploy FortiGate Next-Generation Firewalls
Why Use FortiGate? The cloud often connects with on-premises resources, which presents a risk. FortiGate Next-Generation Firewalls (NGFWs) are essential for securing traffic between your on-premises data center and cloud infrastructure. These firewalls offer real-time threat intelligence, application-aware filtering, and intrusion prevention to protect against threats.
Benefits of FortiGate in Cloud Security:
- Deep packet inspection (DPI) of encrypted traffic
- Advanced threat protection with FortiGuard AI-driven intelligence
- Scalable performance to handle high-volume cloud traffic
Implementation Tip: Deploy FortiGate as a virtual appliance within your cloud platform (AWS) to inspect and filter both inbound and outbound traffic. Use segmentation to isolate workloads and apply policies based on the sensitivity of data and applications
Cloud-Native Integration
Fortinet’s Integration with Cloud Platforms To fully leverage Fortinet’s security tools, it’s critical to integrate them into your cloud infrastructure. Fortinet integrates seamlessly with major cloud service providers like AWS, Azure, and Google Cloud, providing visibility and control over cloud-native applications and workloads.
Fortinet Cloud Security Services:
- FortiCASB (Cloud Access Security Broker): Helps monitor, control, and secure data stored in cloud applications.
- FortiWeb: Secures web applications from common threats like cross-site scripting (XSS), SQL injection, and DDoS attacks.
- FortiMail: Protects cloud email systems from phishing, malware, and spam.
Implementation Tip: Ensure that Fortinet tools are configured to auto-scale with cloud resources, enabling them to adapt to dynamic cloud environments. This helps maintain consistent security without compromising performance during workload surges.
Employ a Multi-Layered Security Approach
Why Layered Security Matters
A single security solution is never enough. Employing a multi-layered approach provides different layers of defense, ensuring that even if one measure fails, others remain in place to stop potential threats.
Fortinet’s Layered Security Tools:
- FortiWeb: Web application security to protect cloud-hosted apps.
- FortiMail: Email security for Office 365, G Suite, and other cloud platforms.
- FortiSandbox: Advanced threat detection to identify zero-day vulnerabilities.
Implementation Tip: Use Fortinet’s Security Fabric to connect different layers of protection. For example, if FortiGate detects unusual traffic, FortiSandbox can analyze the content for potential malware, while FortiMail will block malicious attachments.
Continuous Monitoring and Threat Intelligence
The Importance of Continuous Monitoring
Threats evolve continuously, making real-time monitoring a necessity for any cloud environment. Fortinet provides several tools that facilitate proactive threat detection and response.
Tools for Monitoring:
- FortiSIEM: Fortinet’s Security Information and Event Management (SIEM) tool aggregates data from multiple sources, including cloud applications and networks, for real-time visibility.
- FortiGuard Threat Intelligence: Continuously updates Fortinet’s security products with the latest threat data, enabling quicker identification and mitigation of threats.
Implementation Tip: Integrate FortiSIEM with cloud logging services like AWS CloudTrail or Azure Monitor to ensure holistic monitoring across all cloud resources. This enables quicker detection and response to anomalies or potential security breaches.
Automate Compliance Management
Why Compliance Matters
Compliance with industry regulations such as GDPR, HIPAA, and PCI-DSS is critical for cloud environments, especially those handling sensitive or financial data. Fortinet’s tools are designed to help meet compliance requirements by offering secure data handling and reporting features.
Fortinet for Compliance:
- FortiAnalyzer: Provides detailed logs and reports to ensure audit trails and compliance documentation.
- FortiGate: Enables secure encryption and decryption policies for sensitive data.
Implementation Tip: Regularly audit your cloud environment using FortiAnalyzer to ensure that your organization meets its regulatory requirements. Automate compliance checks where possible to avoid human error and reduce workload.
Conclusion
By adopting Fortinet’s suite of cloud security solutions, you can achieve robust security across your cloud infrastructure. A comprehensive approach involving Zero Trust, NGFWs, cloud-native integration, and continuous monitoring is critical in today’s evolving threat landscape. With these best practices, you can fortify your cloud security posture, ensuring that your data and applications remain protected from modern cyber threats.
Whether you are a small, medium, or large enterprise, or a public sector organization, we are your partner with the right skills and experience to help you move your business forward.